Secure boot
Protect against vulnerabilities at boot time
Computers are vulnerable during the boot process if they are not secured. The kernel, hardware peripherals and user space processes are all initiated at boot and any vulnerability in the boot firmware can have cascading effects on the entire system.
In the case of an attack on boot firmware, damages are so profound that often hardware replacement is the only fix. In an industrial IoT scenario, this means considerable downtime, manual maintenance, possibly at several locations and CapEx for hardware replacement. An utterly undesirable outcome.
Integrity verification
The integrity of the boot firmware must be proven before trust is established in user space processes. This requires a secure mechanism to establish integrity.
Such a mechanism should be implemented into low level computer initialisation firmware like UEFI, as validating the boot process integrity at this low level assures that a device has started up in a secure state.
Standard requirements and recommendations for boot integrity measurement are following (NIST 800-155):
- Enable endpoints to measure the integrity of all executables and configuration metadata at boot time
- Securely transmit measurements of integrity
- Provide the hardware support necessary to implement credible root of trust for integrity measurements
The root of trust is the most critical element for integrity determination. It can be implemented in hardware through secure elements or Trusted Platform Module (TPM) or coded in software using cryptographic libraries (Trusted Execution Environment).
Secure boot on Ubuntu Core
ARM and x86
Ubuntu Core abstracts the root of trust implementation for its secure boot process. As a consequence, Ubuntu Core secure boot can be enabled for both ARM and x86 SoCs.
Free for pre-certified boards
Secure boot is available out of the box on certified devices at no additional cost. An enablement fee is required to fully certify Ubuntu Core on non-certified boards.
How it works
Since Ubuntu Core 20, the boot process is authenticated by default. Authentication is based on the verification of digital signatures.
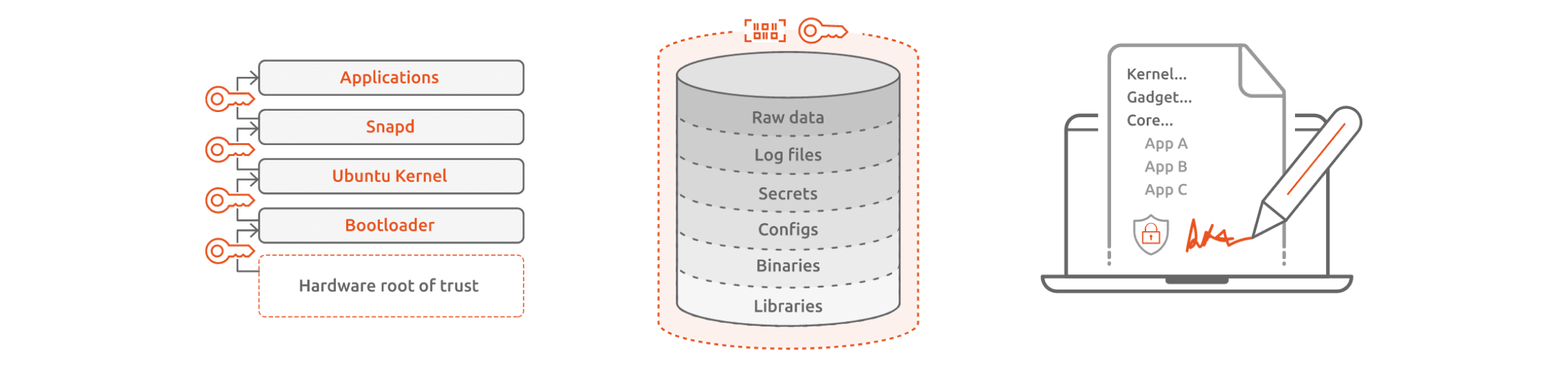
Chain of Trust
Each component in the boot sequence cryptographically validates the authenticity of the subsequent component in the boot sequence. Every component is measured before it is loaded in the runtime memory space. If an improper or unsigned component is detected, the boot process is stopped.
Digital keys
Ubuntu Core supports both hardware and software root of trust for secure boot. Security admins can create and store the digital keys used to validate the boot sequence in either a secure element, a TPM device or a software TEE.

Secure your devices
Get in touch with a Ubuntu security expert to discuss the advanced security requirements of your application.
